Ingest Software Bill of Materials (SBOM) data into SSCA
A Software Bill of Materials (SBOM) is a list of all the components, libraries, and other dependencies used in a software application. Harness SSCA can ingest JSON SPDX or CycloneDx formatted SBOM from any tool that can generate these report formats.
Use this configuration for scanners that don't have built-in support in SSCA. For scanners with built-in support you can:
- Use the SSCA Orchestration step to generate SBOM.
- Ingest results from a Blackduck STO scan step.
- Ingest results from an Aqua Trivy STO scan step.
For a list of all SSCA-supported scanners, go to What's supported for STO.
Generate a key pair
Keys are used to sign and verify attestations.
- Generate a public and private key pair. For example, you can use Cosign to generate key pairs.
- Create two Harness file secrets, one for the private key file and one for the public key file.
- Create a Harness text secret to store the password for the private key.
Configure your pipeline to ingest SBOM
-
In your Harness pipeline, go to the stage where you want to ingest the SBOM, and select the Overview tab.
-
In Shared Paths, enter a path to a location where your SBOM can be stored on the build machine, such as
/shared/customer_artifacts.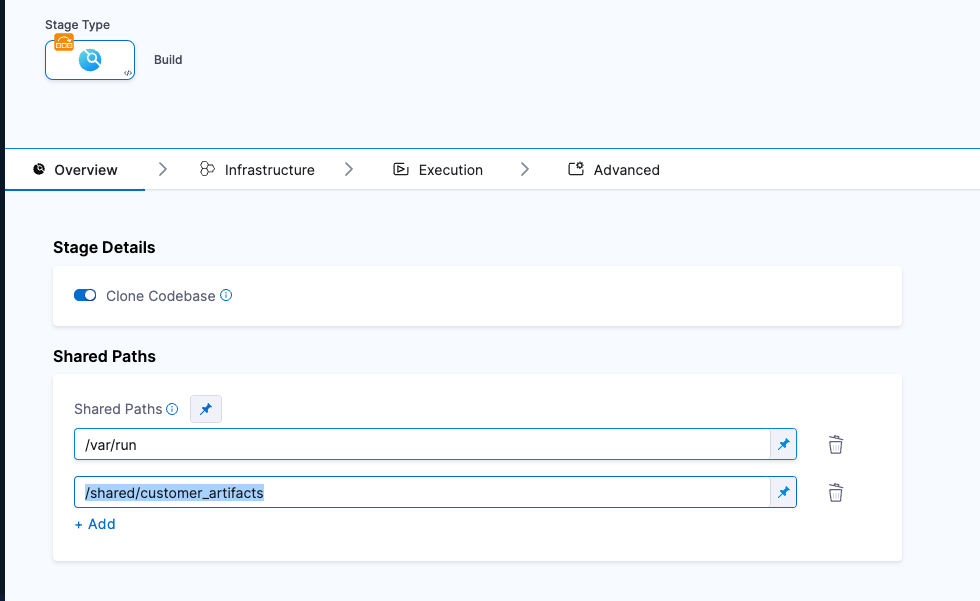
-
Add a step to your stage that generates an SBOM, such as a Run, Plugin, or GitHub Action step.
For example, this Run step uses Aqua Trivy to generate an SBOM.
trivy image \
--format spdx-json \
--output /shared/customer_artifacts/result.spdx.json \
ubuntu:22.04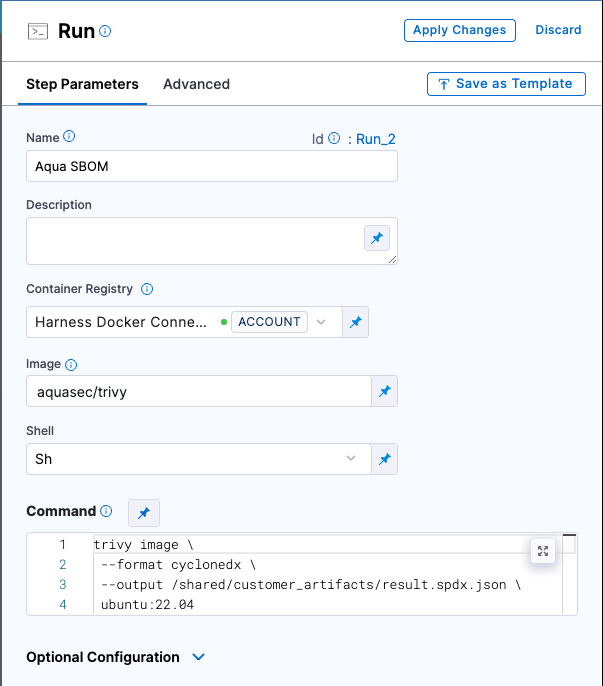 tip
tipYou can also configure pipelines to ingest SBOM from STO scanner steps.
-
If your SBOM tool can't output directly to your Shared Path, then add commands or a Run step to copy the SBOM into the directory specified in Shared Paths.
-
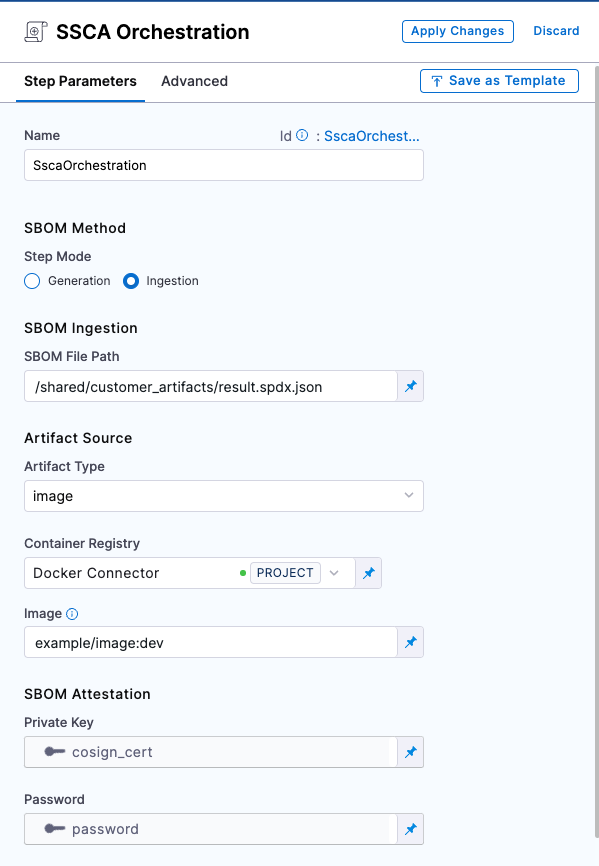
Add an SSCA Orchestration step configured to ingest the SBOM:
- Set the Step Mode to Ingestion.
- For SBOM File Path, enter the path to the SBOM file generated by your SBOM tool.
- For Container Registry, select the Docker Registry connector that is configured for the Docker-compliant container registry where you stored the artifact associated with the SBOM, such as Docker Hub, Amazon ECR, or GCR.
- For Image, enter the repo path (in your container registry) and tag for the image associated with the SBOM, such as
my-docker-repo/my-artifact:latest. - Private Key: The Harness file secret containing the private key to use to sign the attestation.
- Password: The Harness text secret containing the password for the private key.
If you're using Docker-compliant ECR or GCR repositories, you must:
- Configure your Docker Registry connector as a valid artifact source.
- For ECR, go to Use Docker Registry for ECR.
- For GCR, go to Use Docker Registry for GCR
- Use the full URI for the Image in your SSCA Orchestration step, such as
1234567890.dkr.ecr.REGION.amazonaws.com/IMAGE_NAME:TAG.